What is email spoofing?
Email spoofing is a security threat in which hackers send emails impersonating a legitimate organization's or sender's identity. Threat actors send spoofed emails to trick recipients into believing that they're authentic and nudge them to perform sensitive actions.
Email spoofing types
Email spoofing is a common threat that costs businesses huge amounts of money.
2
millionOrganizations lose $2 million every year due to brand impersonation
40
spoofed domainsThe average brand faces 40 spoofed domain attacks per month
Spoof protection
Keeping your organization's mailboxes guarded from hackers mandates implementing a well-rounded security solution that detects spoofing of your organization's executives, suppliers, vendors, and other trusted domains.
The benefits of spoof protection
Shield your business from spoofed vendor domains
Steer your users' mailboxes away from emails sent using spoofed vendor domain names. Hackers impersonate prominent vendor domains and send emails that mimic regular payment and invoice requests.

Protect your users from impersonated display names
Ensure that your users don't fall prey to payment or information requests sent with spoofed display names of high-profile executives such as the CEO or CFO. Threat actors send such impersonated emails by researching the company's communication patterns.

Rest assured with email authentication
Stay confident that all of the emails that reach your users' mailboxes have passed the basic authentication checks, such as SPF, DKIM, and DMARC. Emails sent with malicious intent often fail these checks and are identified during email reception.
eProtect's spoof protection
eProtect offers a rich set of features that protects your organization from spoofed domains and display names.
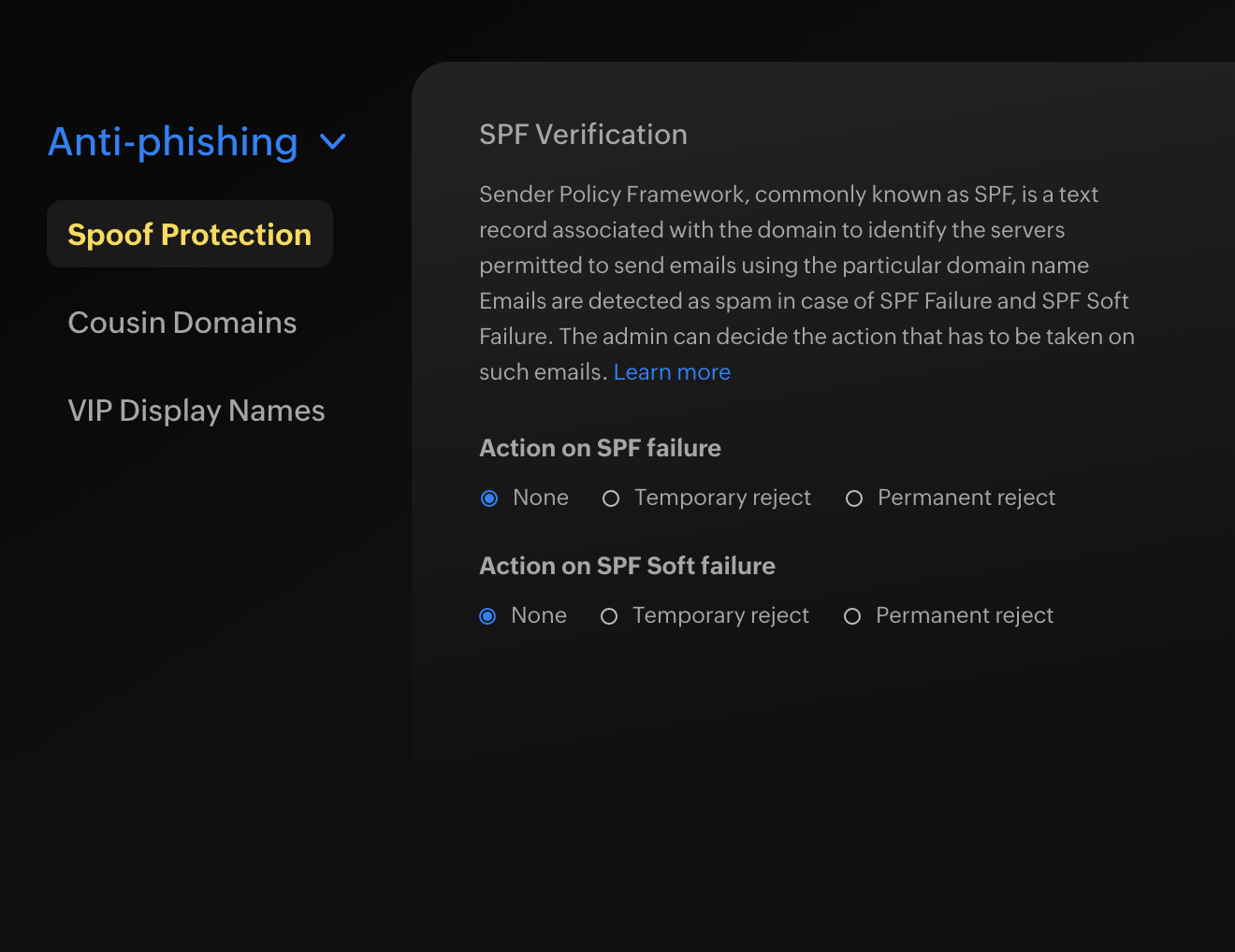
Authentication protocols
With eProtect, you can choose the action to be performed on emails that fail the SPF, DKIM, or DMARC authentication protocols. You can define the settings for each protocol and decide whether to reject the emails or quarantine them.
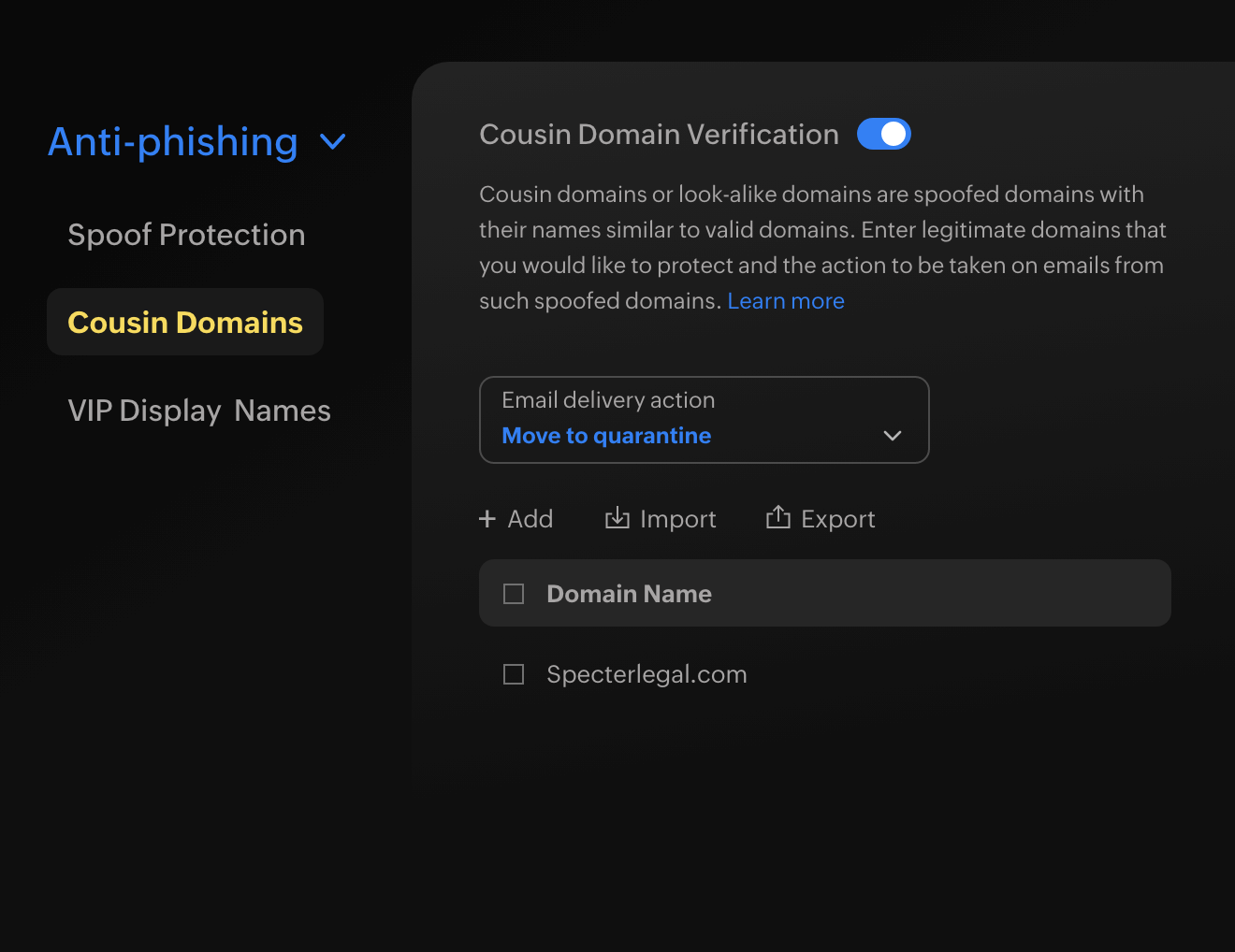
Domain impersonation protection
Configure domain names that you closely interact with in eProtect and we'll make sure similar domain names are promptly identified and processed. Such emails are either marked as spam or quarantined based on your preferences.
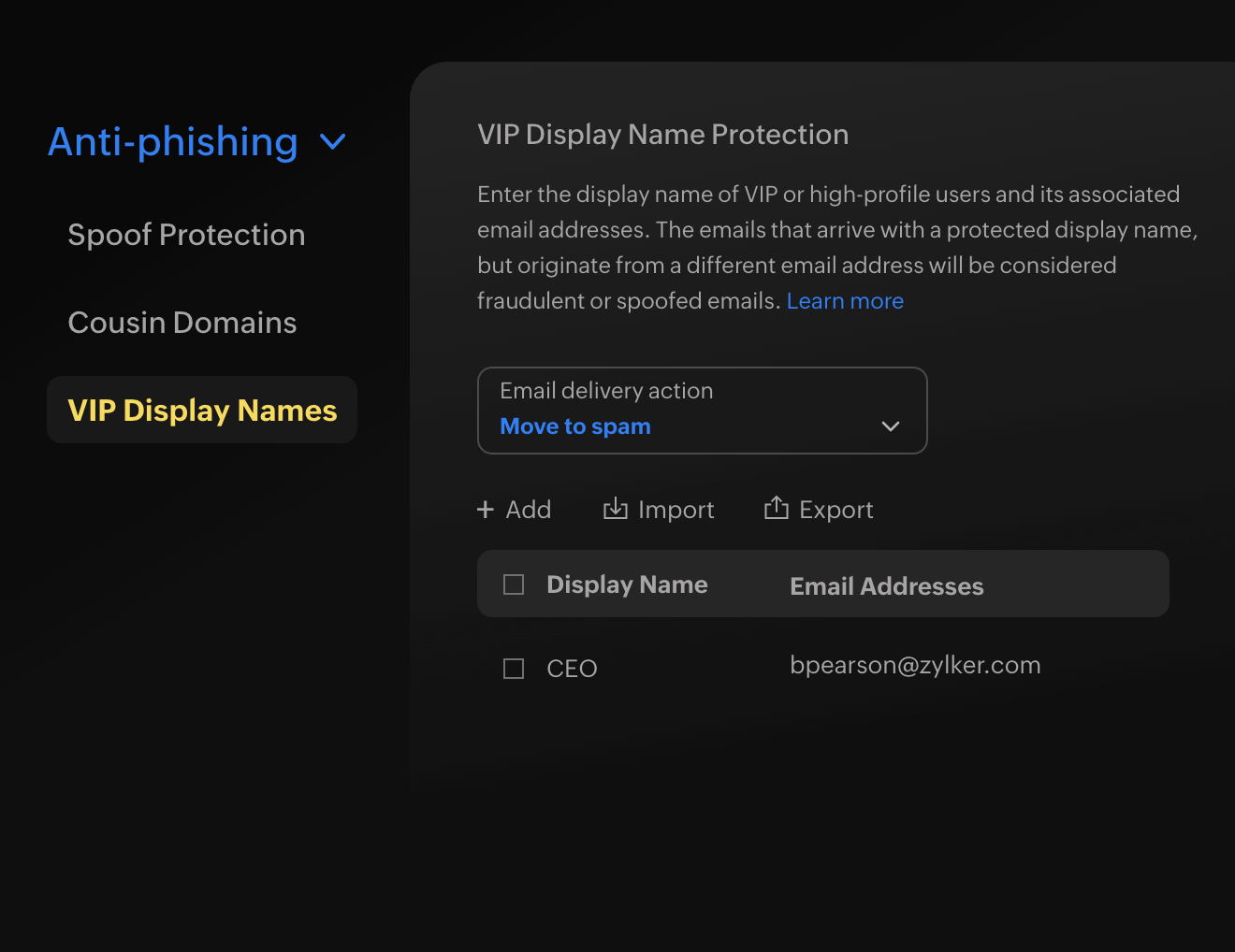
Display name protection
Associate specific email addresses with display names, making sure all other email addresses sent containing that display name are flagged and handled accordingly. Your users can stay protected from all emails mimicking a certain display name.
Comprehensive reports
Get a birds-eye view of the different threat types that have been blocked and the authentication failures that have occurred with eProtect's comprehensive dashboard. This helps you tweak your security policy to attain top-notch security for your emails.




Frequently Asked Questions
How to protect from email spoofing?
You can protect your organization from email spoofing by enabling the spoof protection features available in eProtect. Additionally, it’s also essential that you conduct security awareness trainings to familiarize your employees about the workings of spoofed emails.
How does spoof protection work in eProtect?
eProtect offers a range of spoof protection features such as SPF, DKIM, and DMARC authentication mechanisms, cousin domains, and VIP display names protection to keep spoofed emails away from your mailboxes.
What happens if we disable spoof protection?
We strongly recommend that you configure the spoof protection features available in eProtect. Disabling them might put your mailbox at risk of encountering spoofed emails.
How to identify a suspicious email?
One way to identify a spoofed email is by verifying the display name, email address, and domain name of the sender. If you find any inconsistencies among these, avoid engaging with the email and get in touch with your email administrator.
What to do if you're spoofed?
If you realize that you’ve received a spoofed email, ensure that you don’t click on any links or download any attachments present in the email. Inform your organization’s email administrator about the same so they can customize the security policies and inform other users about the same. Finally, report the email as spam.
Achieve top-notch spoof protection for your emails
Contact Sales


